Identity Analysis
Identity Analytics - Oort
Identity analytics helps decision-makers like CISOs and CIOs to comprehend and predict the effects of identity and access management on their organization. This is done by gathering critical information regarding user behavior and key factors relevant to them, for example, trust, reputation, risk exposure, and costs.
https://oort.io/identity-analytics/
Identity (Analysis)—ArcGIS Pro | Documentation - Esri
Summary Computes a geometric intersection of the input features and identity features. The input features or portions thereof that overlap identity features will get the attributes of those identity features. Illustration Usage The Input Features parameter value can be point, multipoint, line, or polygon.
https://pro.arcgis.com/en/pro-app/latest/tool-reference/analysis/identity.htm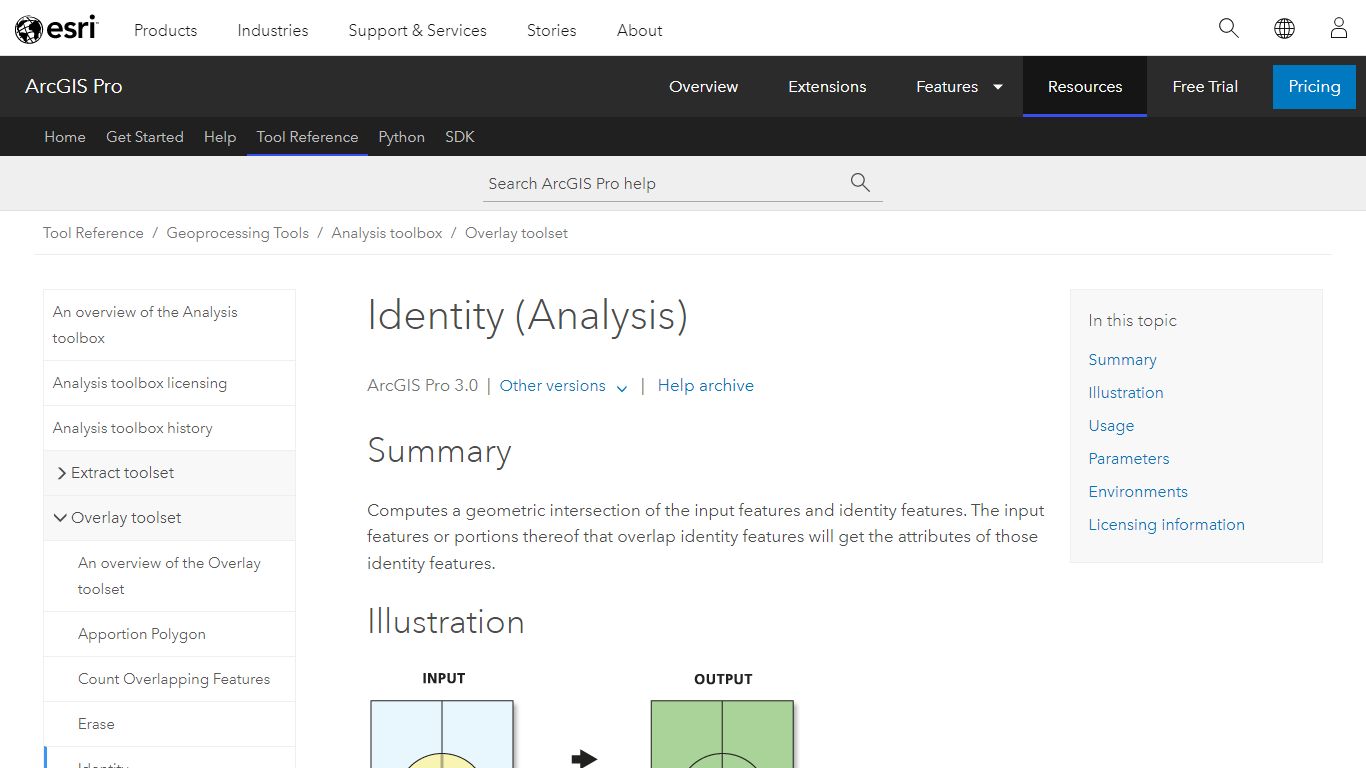
Identity (Analysis)—ArcMap | Documentation - Esri
The following Python window script demonstrates how to use the Identity function in immediate mode. import arcpy from arcpy import env env.workspace = "c:/data/data.gdb" arcpy.Identity_analysis("wells", "counties", "wells_w_county_info") Identity example 2 (stand-alone Python script)
https://desktop.arcgis.com/en/arcmap/latest/tools/analysis-toolbox/identity.htm
Identity Analysis - eNotes.com
Despite this reception, Identity is notable for the author’s insight into the interplay between the individual’s preoccupations and the social, public self, and for his continuing uncanny ability...
https://www.enotes.com/topics/identity/in-depth
Identity (Analysis)—ArcGIS Pro | Documentation - Esri
Summary Computes a geometric intersection of the input features and identity features. The input features or portions thereof that overlap identity features will get the attributes of those identity features. Illustration Usage Input Features can be point, multipoint, line, or polygon.
https://pro.arcgis.com/en/pro-app/2.7/tool-reference/analysis/identity.htm
Identity—Help | ArcGIS for Desktop - Esri
Summary Computes a geometric intersection of the input features and identity features. The input features or portions thereof that overlap identity features will get the attributes of those identity features. Illustration Usage Input Features can be point, multipoint, line, or polygon.
https://desktop.arcgis.com/en/arcmap/10.3/tools/analysis-toolbox/identity.htm
Identity protection risk analysis workbook in Azure AD - Microsoft ...
In this article. Azure AD Identity Protection detects, remediates, and prevents compromised identities. As an IT administrator, you want to understand risk trends in your organizations and opportunities for better policy configuration. With the Identity Protection Risky Analysis Workbook, you can answer common questions about your Identity ...
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/workbook-risk-analysis
Identity Movie Plot Ending, Explained - The Cinemaholic
Identity Ending, Explained. A phenomenal thriller reminiscent of the Agatha Christie’s ‘And Then There Were None’ took the world by storm in 2003. It was a ‘whodunnit’ film albeit a groundbreaking twist which completely threw its audience off guard. In this article, I aim to explain the plot details of the film which are slightly ...
https://thecinemaholic.com/identity-explained/
Identity Proofing and Credential Analysis - Secretary of State of Texas
Identity proofing is the means by which the principal (signer of a document) affirms their identity. This is done through a third party who uses dynamic knowledge based authentication (KBA). KBA is a process in which the principal is asked a series of questions about the principal’s identity and personal history. In order to pass, the ...
https://www.sos.state.tx.us/statdoc/identityproofing.shtml
Identity movie review & film summary (2003) | Roger Ebert
Identity. It is a dark and stormy night. A violent thunderstorm howls down on a lonely Nevada road. A family of three is stopped by a blowout. While the father tries to change the tire, his wife is struck by a passing limousine. Despite the protests of the limo's passenger, a spoiled movie star, the driver takes them all to a nearby motel.
https://www.rogerebert.com/reviews/identity-2003